
The cybersecurity landscape is fraught with challenges that organizations must navigate to protect their assets and data effectively. Among these challenges are the emergence of advanced threats, the increasing complexity and sophistication of attacks, and a significant skills gap in the workforce.
Evolving Threat Landscape
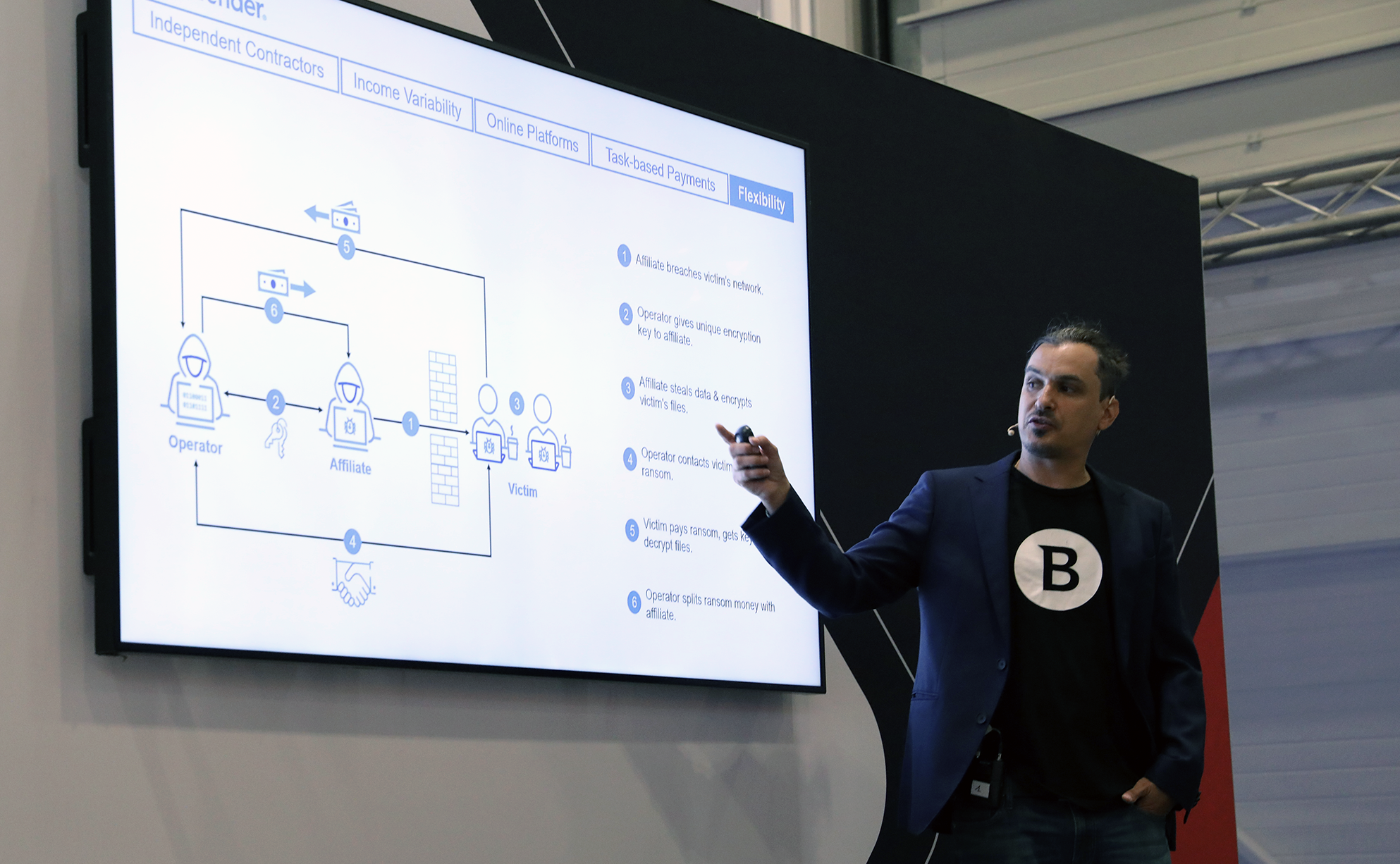
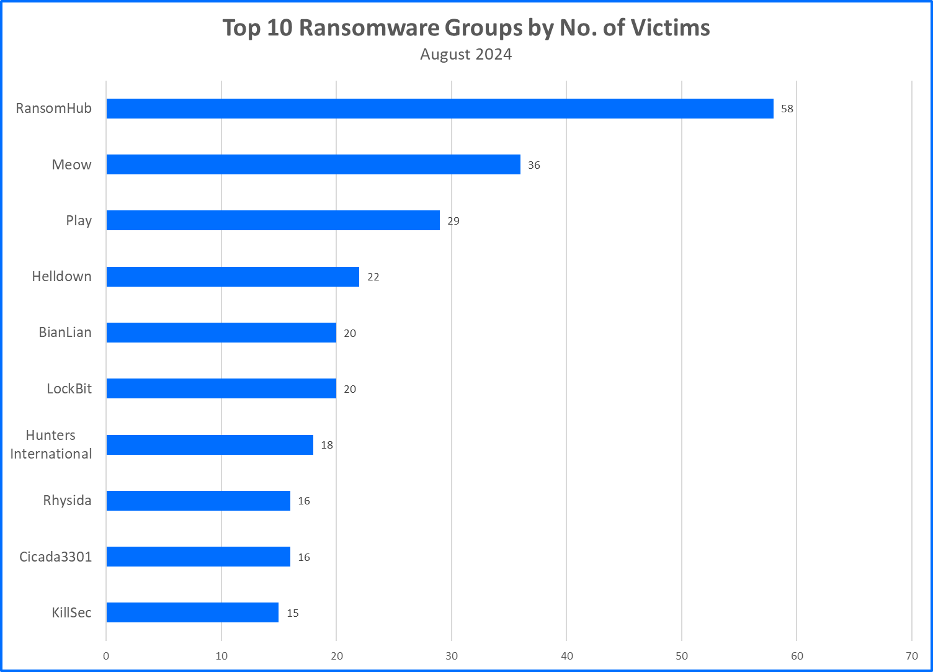
Cybercriminals are diversifying their tactics, making the threat landscape more volatile than ever. The projected costs of cybercrime are expected to skyrocket, reaching $10.5 trillion by 2025, underscoring the urgent need for organizations to bolster their security measures to counteract these escalating risks[11]. One of the most prominent threats comes from ransomware, which continues to plague organizations across various sectors. In 2024, healthcare, government, and critical infrastructure sectors remain particularly vulnerable, as these industries are prime targets for ransomware attacks that maximize potential returns for cybercriminals[4][5].
The sophistication of attacks has also increased, with adversaries employing methods such as identity theft and phishing that exploit vulnerabilities within cloud systems[3]. Moreover, generative AI is anticipated to further empower cybercriminals, allowing for more convincing phishing attempts and automated malware, which could give attackers a significant advantage over defenders in the coming years[10][11].
Regulatory and Compliance Pressures

As cyber threats evolve, so do the regulatory environments that govern how organizations must protect sensitive information. The introduction of stringent regulations, such as the EU's Network and Information Systems Directive 2 (NIS2), emphasizes the need for compliance with specific cybersecurity measures[2]. Organizations face ever-tightening legal requirements aiming to enhance cybersecurity resilience, which necessitates a proactive approach to incident reporting and compliance adherence.
The fragmented regulatory landscape also presents challenges, with 34% of leaders reporting that too many conflicting regulations create difficulties in compliance[11]. This complexity can result in inconsistencies in cybersecurity practices across different jurisdictions and industries, further complicating organizations' efforts to maintain security.
Skills and Workforce Shortages

A significant and ongoing challenge is the shortage of skilled cybersecurity professionals. Reports indicate that the cybersecurity skills gap has worsened, with 54% of cybersecurity professionals stating that the skills shortage has negatively impacted their organizations[6][4]. As operations increasingly shift to digital and cloud environments, the demand for cybersecurity expertise will continue to rise, leaving organizations scrambling to fill critical roles.
The high turnover rate in the cybersecurity workforce, particularly in the European Union where it's reported to exceed 20%, compounds these challenges. Organizations are finding it essential to not only attract new talent but also retain existing employees through upskilling initiatives and making cybersecurity roles more appealing[2][4]. Upskilling current employees is becoming a prevalent strategy since many organizations report a willingness to invest in cybersecurity training and certifications to equip employees with the necessary skills[11].
Financial Implications of Cyber Threats

The financial implications of cyber threats are enormous and growing. The cost of data breaches has risen, with the average cost of a breach reaching $4.45 million in 2023, marking a 15% increase compared to previous years[11]. Additionally, remote work environment vulnerabilities have led to breaches costing an average of $173,074 more than in strictly on-site operations[11]. This financial burden is worsened by rising cyber insurance premiums, which surged by 50% in 2022, making it difficult for small to medium enterprises to secure adequate coverage without significant investment[11].
As ransomware attacks continue to evolve, the use of extortion tactics, including double and triple extortion, further complicates recovery efforts and increases costs[5][8]. The average ransomware payout has jumped significantly, illustrating how organizations must navigate both direct ransom payments and the higher costs associated with recovery from attacks[11].
Supply Chain and Ecosystem Challenges
The interconnected nature of today's digital ecosystem introduces additional vulnerability. Supply chain risks have become a focal point for many cybersecurity discussions, with 41% of organizations acknowledging that material incidents in the past year originated from third-party providers[10]. This signifies the necessity for organizations to not only assess their cybersecurity posture but also that of their supply chain partners. However, many report insufficient visibility into supply chain vulnerabilities, hindering their capacity to manage risks effectively[6][10].
Organizations face pressure to enhance their overall ecosystem resilience while addressing individual weaknesses within their supply chains. This effort requires collaboration between organizations, regulatory bodies, and industry partners to collectively bolster security measures and infrastructure against systemic threats.
Conclusion
Cybersecurity today is marked by an evolving landscape filled with sophisticated threats, regulatory pressures, and a critical shortage of skilled professionals. The financial implications of these challenges are substantial, and the interconnected nature of digital infrastructures necessitates a comprehensive approach to mitigate risks. As we advance further into 2024, organizations must adopt proactive strategies, invest in talent development, and enhance collaboration across every facet of their operations to secure their assets effectively and respond to the relentless tide of cyber threats.
Get more accurate answers with Super Pandi, upload files, personalized discovery feed, save searches and contribute to the PandiPedia.
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).