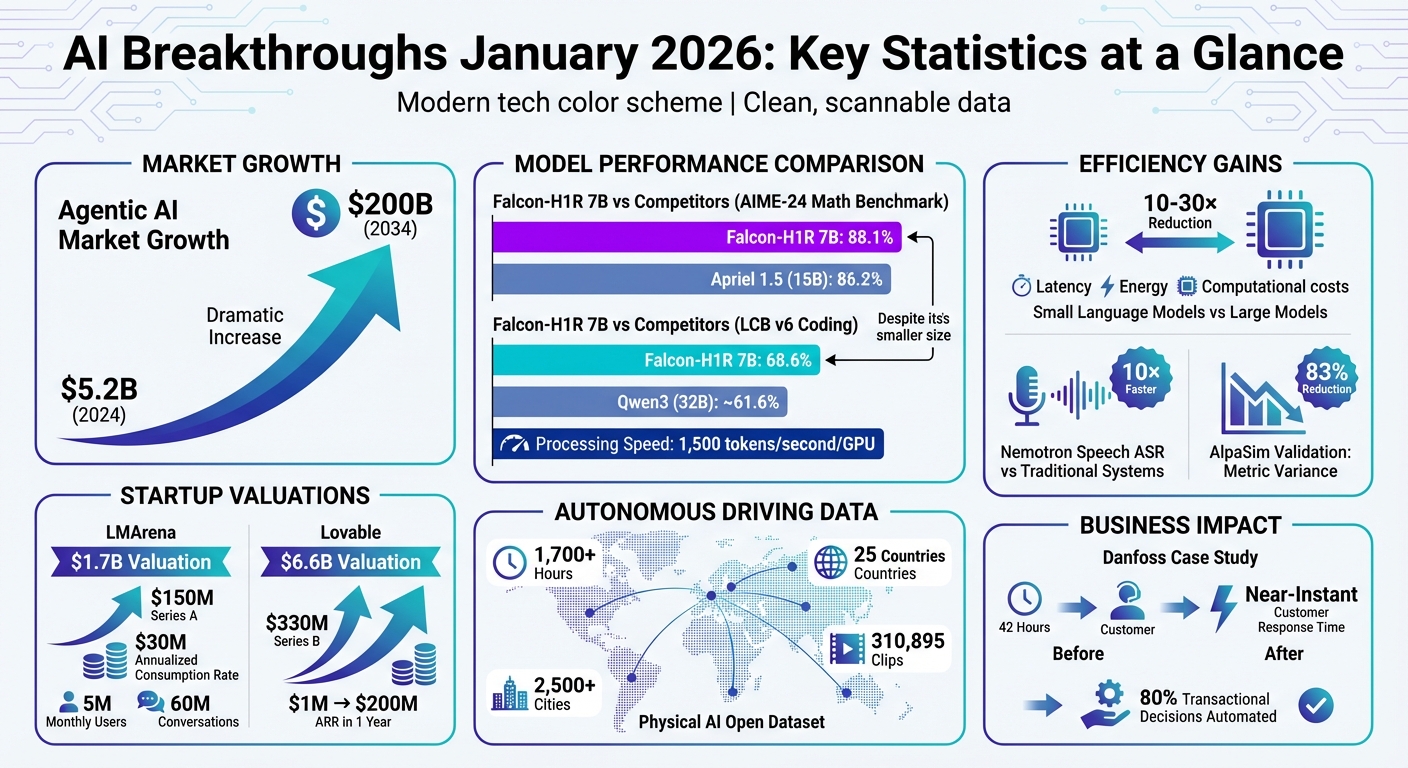
Legendary AI Papers
Highlights pivotal research papers in artificial intelligence that have had significant impacts on the field.
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).
In recent years, natural language processing (NLP) has seen significant advancements thanks to models like BERT (Bidirectional Encoder Representations from Transformers). BERT introduces a unique way of processing words that allows for a deeper understanding of context, which is critical for various language-related tasks.
Introduction to BERT
The Core Concept of BERT
BERT utilizes a bidirectional approach, meaning that it considers the context from both the left and the right of a word simultaneously. This is a significant shift from traditional methods that analyzed text in a linear fashion, moving left-to-right or right-to-left. The model's ability to create deep contextual representations of words has been shown to improve performance on a variety of tasks, such as question answering and language inference[1].
Pre-training Tasks
BERT is pre-trained using two tasks: Masked Language Model (MLM) and Next Sentence Prediction (NSP). The MLM involves randomly masking some percentage of the input tokens and predicting them based on their context. This enables the model to learn bidirectional representations efficiently. The NSP task helps BERT understand relationships between sentence pairs, thereby enhancing its ability to comprehend the flow of text[1].
Masked Language Model (MLM)
In MLM, a percentage of the words in a sentence are masked, and the model learns to predict these masked words, allowing it to grasp grammatical structure and contextual meaning. For instance, if the sentence 'The cat sat on the [MASK]' is provided, BERT aims to predict the masked word based on the surrounding words[1].
Next Sentence Prediction (NSP)
The NSP task involves predicting whether a given sentence logically follows another. For example, if the input is 'The man went to the store. He bought milk.', BERT assesses whether this is a coherent pair. This task is crucial for applications requiring an understanding of how sentences relate to each other[1].
Applications of BERT
BERT has transformed the field of NLP, demonstrating improved performance on benchmarks such as the General Language Understanding Evaluation (GLUE) and various specific tasks like question answering (SQuAD) and sentiment analysis. For example, BERT significantly outperformed previous models on SQuAD, achieving test scores that set new standards[1].
Sentence Pair Classification
Tasks such as MNLI (Multi-Genre Natural Language Inference), QNP (Question Natural Language Processing), and others utilize BERT's ability to process pairs of sentences. By integrating information from both sentences, BERT can make more informed predictions about their relationships[1].
Single Sentence Classification and tagging
BERT also excels in tasks that involve a single sentence. For instance, it can effectively classify the sentiment of a review or identify named entities within a text. This flexibility is one of the reasons BERT has become a foundational model in NLP[1].
Fine-Tuning BERT for Specific Tasks
After pre-training, BERT can be fine-tuned on specific tasks. This process is straightforward and involves initializing with the pre-trained parameters, then training with labeled data for the target task. During fine-tuning, BERT's self-attention mechanism helps it to adapt its representations for the nuances of the given task while retaining its learned contextual knowledge[1].
Advantages of Fine-Tuning
Fine-tuning has proven to be effective across diverse applications, maintaining high accuracy levels while requiring comparatively less labeled data than usual. The ability to fine-tune BERT for various tasks allows practitioners to utilize its powerful representations without needing extensive computational resources[1].
Impact and Future Directions
The introduction of BERT has sparked a new wave of research and development in NLP. Its ability to handle tasks requiring a nuanced understanding of language has led to its adoption in numerous projects and applications beyond academia, including industry solutions for chatbots, search engines, and more.
As language models continue to evolve, the foundational ideas introduced by BERT will likely influence the design of future architectures. The ongoing research into improving these models will focus on enhancing their efficiency and capability to handle more complex linguistic tasks[1].
Conclusion
The emergence of BERT signifies a pivotal moment in the field of NLP. By leveraging bidirectional context and sophisticated pre-training techniques, it has set new benchmarks for language understanding tasks. As researchers build upon its architecture, we can expect further advancements that will expand what is possible in the realm of artificial intelligence and machine learning.
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).
Get more accurate answers with Super Pandi, upload files, personalised discovery feed, save searches and contribute to the PandiPedia.
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).

The core challenge in continual learning for Large Language Models (LLMs) is catastrophic forgetting, where models degrade performance on old tasks when trained on new data[2][3][4]. The massive scale of LLMs introduces a huge computational burden for frequent retraining, requiring efficient adaptation to evolving data while balancing general capabilities with new task learning[2][4]. Handling non-IID data and avoiding destructive gradient updates from external data are critical[3].
Additional challenges arise from multi-stage training, including task heterogeneity, inaccessible upstream data, long task sequences, and abrupt distributional shifts[2]. There is a need for practical evaluation benchmarks, computationally efficient methods, controllable forgetting, and history tracking[2][4]. Theoretical understanding of LLM forgetting and memory interpretability remain significant hurdles[2][4].
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).

Nested Learning (NL) fundamentally differs from traditional deep learning architectures by reframing how machine learning models learn and operate[1][2][3][4][5].
Here are the key distinctions:
* Nature of the Model and Learning Process: Traditional deep learning views models as static structures, where learning occurs during a separate training phase, after which the model is considered complete and performs fixed computations during inference[2][6]. Nested Learning, however, represents a model as a coherent system of nested, multi-level, and/or parallel optimization problems, each with its own 'context flow' and update frequency[1][3][4][5]. It argues that learning happens inside learning, across multiple levels and speeds, even during inference[2][6].
* Source of Intelligence: Traditional architectural thinking assumes intelligence emerges primarily from architectural depth, such as stacking more layers[6]. NL challenges this, proposing that intelligence arises from how learning itself is organized across multiple levels, time scales, and memory systems[6]. It suggests that many successes attributed to deep architectures are better understood as 'learning-within-learning' hidden inside optimization, memory updates, and inference-time adaptation[6].
* Role of Optimizers: In traditional deep learning, optimizers like SGD or Adam are treated as external algorithms used merely to adjust weights during training[6]. NL reinterprets these gradient-based optimizers as associative memory modules that aim to compress gradients[1][3][4][5]. From the NL viewpoint, optimizers are learning systems themselves, storing knowledge about the loss landscape and influencing how parameters evolve[4][6].
* Memory System: Traditional models often imply a clear distinction between 'long-term' and 'short-term' memory residing in distinct brain structures[3][4]. NL introduces the 'Continuum Memory System' (CMS), which generalizes this traditional viewpoint by seeing memory as a distributed, interconnected system with a spectrum of frequency updates[1][3][4][5]. Higher-frequency components adapt quickly, while lower-frequency components integrate information over longer periods[2].
* Continual Learning and Adaptation: Large Language Models (LLMs) in traditional deep learning are largely static after pre-training, unable to continually acquire new capabilities beyond their immediate context, akin to 'anterograde amnesia'[2][3][4]. NL provides a mathematical blueprint for designing models capable of continual learning, self-improvement, and higher-order in-context reasoning by explicitly engineering multi-timescale memory systems[2].
* Computational Depth: While traditional deep learning measures depth by the number of layers, NL introduces a new dimension to deep learning by stacking more 'levels' of learning, resulting in higher-order in-context learning abilities and enhanced computational depth[1][3][4][5][6].
* In-Context Learning: NL reveals that existing deep learning methods learn from data through compressing their own context flow, and explains how in-context learning emerges in large models[1][3][4][5]. From the NL perspective, in-context learning is a direct consequence of having multiple nested levels, rather than an emergent characteristic[3][4].
* Architectural Uniformity: NL suggests that modern deep learning architectures are fundamentally uniform, consisting of feedforward layers (linear or deep MLPs), with differences arising from their level, objective, and learning update rule[3][4]. The apparent heterogeneity is an 'illusion' caused by viewing only the final solution of optimization problems[3][4].
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).

Test-time compute (TTC) enhances AI reasoning accuracy by allowing models to dynamically allocate computational resources based on task complexity. This means that instead of using a fixed amount of computing power for all queries, models can 'think harder' for more challenging problems. For example, OpenAI's latest models can engage in iterative processes, refining their answers through multiple computation steps before delivering a final output[2][6].
By implementing strategies like Chain-of-Thought reasoning, AI models can break down complex questions into manageable parts, improving the quality of their responses significantly. This adaptability leads to better performance in areas requiring deep reasoning, such as mathematics and coding[1][5].
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).
Get more accurate answers with Super Pandi, upload files, personalised discovery feed, save searches and contribute to the PandiPedia.
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).

Reinforcement Learning (RL) has seen significant advancements and diversification over the past few years. This evolution is characterized by improvements in algorithms, increased applicability in various domains, and a deeper understanding of theoretical foundations.
Historical Context and Recent Foundations
Reinforcement Learning as a field is not new; it has a rich history dating back over several decades, with key developments in both theory and application. The foundational concepts were established through a combination of threads, including 'Learning by Trial and Error,' 'The Problem of Optimal Control,' and 'Temporal Difference Learning Methods' ([1]). These concepts collectively converged in the early 1990s, leading to the practical applications of RL in mastering games and complex tasks.
The modern developments in the field have been buoyed by the advent of deep learning, which has allowed RL algorithms to function effectively in high-dimensional spaces. For example, frameworks such as Deep Q-Networks (DQN) and Proximal Policy Optimization (PPO) integrate deep learning methods to enhance policy learning and value function approximation. These approaches marked a significant increase in the performance of RL agents in complex environments, enabling them to reach human-level performance in games like Go and various Atari titles ([2][1]).
Algorithmic Advancements

Recent years have seen a growing variety of RL algorithms tailored to different tasks and environments. Notably, the transformation of traditional RL methods into deep reinforcement learning has led to improvements in sample efficiency and training stability. By employing neural networks, algorithms like DQN have managed to outperform classical approaches, demonstrating robustness against noise and variability in real-world data ([1][2]).
In addition, policy-based methods such as the Actor-Critic framework have gained traction due to their efficiency in dealing with continuous action spaces. These methods offer another layer of sophistication by separating the policy update from the value estimation, allowing for more nuanced decision-making processes ([2]).
Applications Across Various Domains
The versatility of RL has expanded its applications significantly. In finance, RL is increasingly being utilized for various tasks, including optimal trade execution, portfolio management, and market making. Researchers have shown that RL algorithms can make data-driven decisions more effectively than traditional methods based on fixed heuristics. For example, RL techniques have been successfully applied to price financial derivatives, where they adjust to market conditions dynamically without relying on strict parametric models ([2][1]).
One notable application is in optimizing portfolio management strategies where the performance has significantly improved using RL methods compared to classical mean-variance optimization. The RL-derived strategies tend to better adapt to changing market dynamics by continuously learning from market interactions, thereby refining their strategies over time ([2]).
Challenges and Future Directions
Despite these advancements, several challenges remain in the field of RL. Many existing algorithms struggle with sample efficiency, requiring large amounts of data to train effectively. This need can be particularly problematic in financial markets, where historical data can be limited or may not accurately reflect future conditions. Addressing this challenge has led researchers to explore methods that optimize for fewer samples, such as off-policy learning and approaches that leverage past experiences to aid learning in new environments ([1][2]).
Furthermore, the concept of risk-aware RL is gaining attention. Integrating risk metrics into the RL framework is critical for applications where the consequences of decisions can vary significantly, such as trading and investment strategies. This direction hints at a future where RL not only focuses on maximizing returns but also on managing risks in a structured manner ([2]).
Theoretical Developments
The theoretical foundation for RL has been significantly strengthened. Recent studies focus on understanding the convergence properties of various RL algorithms under different conditions, such as using function approximations. Improved understanding of the sample complexity of these methods helps in developing strategies that can better generalize from limited data, which is particularly beneficial in financial applications ([2][1]).
The introduction of risk-sensitive utility formulations in RL allows for a more nuanced consideration of the trade-offs between expected returns and associated risks, particularly in uncertain environments. This evolution towards incorporating real-world financial complexities into the RL setup represents a promising avenue for future research ([2]).
Conclusion
Reinforcement Learning has transformed from a theoretical concept into a powerful tool capable of addressing complex decision-making problems across various industries. The evolution seen in recent years—marked by algorithmic advancements, increased applicability, and refined theoretical understanding—positions RL as a vital component of modern artificial intelligence. Continued research and development in risk management and sample efficiency will further bolster its capabilities, leading to broader adoption and innovative applications in finance and beyond. The future of RL is bright, filled with opportunities for improvement and adaptation to increasingly complex and dynamic environments.
Let's look at alternatives:
- Modify the query.
- Start a new thread.
- Remove sources (if manually added).